J
Jonathan Lee (jlee102)
Guest
Hello with the Containers features now included as a add Windows feature, How can we get a good view of what containers are running? A list or control panel option, or a snap in to add and remove containers on a system?

This photo is from what I assume is live containers running inside this Windows 10 system with a relationship to Hypervisor or VMware inside of Windows Firewall With Advanced security.
I have been wondering for over 9 months now. I found them while running permission tests also pre being seen inside of Windows Firewall and reinstalled the whole OS direct from the Microsoft website wiped out all of the partitions also on the storage drive to get rid of them to check for DCO or HPA hidden issues on the drive, they are back now however I can see them inside of Windows firewall now. I even asked the Professor on our test VMs for class if the base images we had to install for class assignment if we were suppose to find a cyber security issues that were pulled from the College's Azure account. As if it was a pre made autopilot VM with a built in small bug that we as students needed to find. He said no they are clean images used only for learning, so that is out of the question. He reassured me this was not part of the assignment it was clean images. I know I am a student, and learned about containers and using docker in the Windows Server class, so I may now have been wondering more and more and noticed them. However, this is a clean install of Windows 10 OS, a copy that was downloaded directly from Microsoft's website with a activation key from the bottom of the device I own. This is not part of a corporate domain it is private property as well as the software. The only exception is the educational approved VMs for class that are run on hypervisor to learn on.
However I stated to think, with containers now inside of Windows 10, how can I get a docker image list? How can I view what is on the system that relates to the containers in a GUI based list? Where can a admin see containers if it is a Windows feature now. If a system was autopiloted with a invasive set of containers running and you have no way to track them this causes issues in cyber security. If Microsoft adds this now as a feature that says "containers" where is my full container control as administrator and property owner of my system. With Azure and autopilot what if a container is just pushed down on a personal device that is not company owned and it is done so invasively? I start going down routes and ideas as a cyber security student, so where can we find the lists now when I turn this feature on to view and fully have complete visibility of containers. Keep in mind the firewall lists run without the feature enabled.
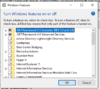
Long story short, where can I see a Microsoft signed list of containers and virus scan them or see the date of when they were installed, time and dates so on?
Where can we see the containers outside of command line?
If we can enable the containers features how can we get a list of them for review?
The professor answered my question there is 3rd party tools.
I do not fully trust Solar Winds products or subsidiaries of that company. This trust issue is caused by issues that happened at work from being forced to use it as soon as Microsoft's Hyperterm software was globally disabled, the company I worked for then directed to us use only the freeware Solar Winds products for tftp for repairing networking equipment. I did not feel that SolarWinds was the approved route upper management wanted. I still wanted to use a Microsoft signed set of software. Software that is fully approved licensed software. Solar Winds is freeware it came with advertisements and other 3rd party software. I am sure there is nothing wrong with a licensed copy. Freeware was not meant to be used on a corporation level. So what's approved for this instance of "container" use? Where is the "signed software" for this function or feature for container management and oversight outside of Microsoft Azure versions. What version for when one is wearing the cyber security pair of spectacles? Keep in mind I have a large bias towards SolarWinds products that was caused by mass email spam advertisements and spam emails for years later and management directed us to use this software for a emergency resolve to fix a failed major networking device the day after Hyperterm was globally disabled and no longer supported with Microsoft and removed via the Microsoft update. I bring this up for a juxtaposition for what companies can do with software and licenses and issues caused by faulty or invasive software or even directing to invasive routes. How can we as cyber security track down invasive issues when they come from the cloud for example, or directed to be used by managers like as my example with SolarWinds. How can we review containers placed or pushed down to a system, maybe a personally owned device. Invasive issues can be pushed from outside sources. Soon we were directed to use only putty another freeware product in the instance of Hyperterm twilighting. If Microsoft can simply remove something as big as Hyperterm with one button, what is to stop and protect a system from someone from just deleting or deploying a invasive container remotely. Oversight.
What is signed how can we check it in this instance?
Because of my bias with Solar Winds I also found Docker Desktop.
Docker Desktop
The real question becomes why does Windows 10 have a feature for "containers" with no ability to manage them in a Windows 10 controlled environment without 2nd party tools? It seems this could cause a security hole on personally owned systems that are not owned by a corporation or managed by them.
Is there a way to manage containers with a "Microsoft signed set of software" that works directly with the Microsoft Windows 10 containers feature set on the endpoint system? What is Microsoft approved? What is Microsoft signed Windows 10 approved container management software? Is there container software outside of Azure that is digitally signed by Microsoft? Like Microsoft's removal and stopping support for Hyperterm and migration to 3rd party software to fill the need, this caused security holes when repairing networking equipment. What is the signed approved software?
We need a Microsoft signed, approved and directed way to interact with the container feature set, just liked I needed a way to use Hyperterm again. With out it there is to many 3rd party security issues that can developed and exploited. Managers even are held hostage and are rapidly searching for a way to replace the Microsoft approved version, like what happened in aged and disabled Hyperterm software. Don't be reckless.
This post is in relation to educational use, and learning.
The lower photos explain container use from Azure cloud side. However with multiple insistences of 3rd party container desktop services you can see the issues I hope to find a solution to. If invasive containers are pushed how can you track the issue to the source if it is cloud accessed and pushed down?


This post is in relation to learning and educational use for cyber security.
Continue reading...
This photo is from what I assume is live containers running inside this Windows 10 system with a relationship to Hypervisor or VMware inside of Windows Firewall With Advanced security.
I have been wondering for over 9 months now. I found them while running permission tests also pre being seen inside of Windows Firewall and reinstalled the whole OS direct from the Microsoft website wiped out all of the partitions also on the storage drive to get rid of them to check for DCO or HPA hidden issues on the drive, they are back now however I can see them inside of Windows firewall now. I even asked the Professor on our test VMs for class if the base images we had to install for class assignment if we were suppose to find a cyber security issues that were pulled from the College's Azure account. As if it was a pre made autopilot VM with a built in small bug that we as students needed to find. He said no they are clean images used only for learning, so that is out of the question. He reassured me this was not part of the assignment it was clean images. I know I am a student, and learned about containers and using docker in the Windows Server class, so I may now have been wondering more and more and noticed them. However, this is a clean install of Windows 10 OS, a copy that was downloaded directly from Microsoft's website with a activation key from the bottom of the device I own. This is not part of a corporate domain it is private property as well as the software. The only exception is the educational approved VMs for class that are run on hypervisor to learn on.
However I stated to think, with containers now inside of Windows 10, how can I get a docker image list? How can I view what is on the system that relates to the containers in a GUI based list? Where can a admin see containers if it is a Windows feature now. If a system was autopiloted with a invasive set of containers running and you have no way to track them this causes issues in cyber security. If Microsoft adds this now as a feature that says "containers" where is my full container control as administrator and property owner of my system. With Azure and autopilot what if a container is just pushed down on a personal device that is not company owned and it is done so invasively? I start going down routes and ideas as a cyber security student, so where can we find the lists now when I turn this feature on to view and fully have complete visibility of containers. Keep in mind the firewall lists run without the feature enabled.

Long story short, where can I see a Microsoft signed list of containers and virus scan them or see the date of when they were installed, time and dates so on?
Where can we see the containers outside of command line?
If we can enable the containers features how can we get a list of them for review?
The professor answered my question there is 3rd party tools.

I do not fully trust Solar Winds products or subsidiaries of that company. This trust issue is caused by issues that happened at work from being forced to use it as soon as Microsoft's Hyperterm software was globally disabled, the company I worked for then directed to us use only the freeware Solar Winds products for tftp for repairing networking equipment. I did not feel that SolarWinds was the approved route upper management wanted. I still wanted to use a Microsoft signed set of software. Software that is fully approved licensed software. Solar Winds is freeware it came with advertisements and other 3rd party software. I am sure there is nothing wrong with a licensed copy. Freeware was not meant to be used on a corporation level. So what's approved for this instance of "container" use? Where is the "signed software" for this function or feature for container management and oversight outside of Microsoft Azure versions. What version for when one is wearing the cyber security pair of spectacles? Keep in mind I have a large bias towards SolarWinds products that was caused by mass email spam advertisements and spam emails for years later and management directed us to use this software for a emergency resolve to fix a failed major networking device the day after Hyperterm was globally disabled and no longer supported with Microsoft and removed via the Microsoft update. I bring this up for a juxtaposition for what companies can do with software and licenses and issues caused by faulty or invasive software or even directing to invasive routes. How can we as cyber security track down invasive issues when they come from the cloud for example, or directed to be used by managers like as my example with SolarWinds. How can we review containers placed or pushed down to a system, maybe a personally owned device. Invasive issues can be pushed from outside sources. Soon we were directed to use only putty another freeware product in the instance of Hyperterm twilighting. If Microsoft can simply remove something as big as Hyperterm with one button, what is to stop and protect a system from someone from just deleting or deploying a invasive container remotely. Oversight.
What is signed how can we check it in this instance?
Because of my bias with Solar Winds I also found Docker Desktop.
Docker Desktop
The real question becomes why does Windows 10 have a feature for "containers" with no ability to manage them in a Windows 10 controlled environment without 2nd party tools? It seems this could cause a security hole on personally owned systems that are not owned by a corporation or managed by them.
Is there a way to manage containers with a "Microsoft signed set of software" that works directly with the Microsoft Windows 10 containers feature set on the endpoint system? What is Microsoft approved? What is Microsoft signed Windows 10 approved container management software? Is there container software outside of Azure that is digitally signed by Microsoft? Like Microsoft's removal and stopping support for Hyperterm and migration to 3rd party software to fill the need, this caused security holes when repairing networking equipment. What is the signed approved software?
We need a Microsoft signed, approved and directed way to interact with the container feature set, just liked I needed a way to use Hyperterm again. With out it there is to many 3rd party security issues that can developed and exploited. Managers even are held hostage and are rapidly searching for a way to replace the Microsoft approved version, like what happened in aged and disabled Hyperterm software. Don't be reckless.
This post is in relation to educational use, and learning.
The lower photos explain container use from Azure cloud side. However with multiple insistences of 3rd party container desktop services you can see the issues I hope to find a solution to. If invasive containers are pushed how can you track the issue to the source if it is cloud accessed and pushed down?
This post is in relation to learning and educational use for cyber security.
Continue reading...