D
David Weston, Vice President Enterprise and OS
Guest
At Microsoft, security is our top priority, and with every release, Windows becomes even more secure. At Ignite 2024, we will highlight new Windows security innovations that will provide the clarity and confidence our customers and organizations require while navigating this evolving digital landscape. We will also talk about our learnings from the July incident, and investments we are making as a result. Protecting your data and ensuring the integrity of your systems is paramount. From chip to cloud, Microsoft provides multiple layers of security to help protect identities and data, and enables an expansive ecosystem for innovation at a critical time. As the security landscape evolves, we continuously enhance Windows' security and resilience, ensuring it remains a secure platform for our partners, developers and customers. A strong security posture is essential for your business, and a shared responsibility across our ecosystem. This week at Ignite, we’re sharing more on our Secure Future Initiative (SFI) — our commitment to making security foundational in everything we do at Microsoft. Since launching SFI, we’ve focused the equivalent of 34,000 full-time engineers on the highest-priority security challenges. The November update dives into insights across all aspects of SFI as well as learnings that customers can implement to strengthen their own security posture. Explore the latest insights and best practices in our November update.
 User prompts for authorizing admin operations[/caption]
User prompts for authorizing admin operations[/caption]
Continue reading...
Security and Resiliency: Our Top Priority
Protecting your organization’s data from emerging threats and ensuring system integrity is paramount. Windows 11 raises the bar for security and reliability, while maintaining the Windows open ecosystem where customers and partners innovate freely. We are committed to ensuring that Windows remains the most reliable and resilient open platform for our customers. As part of this commitment, we are introducing the Windows Resiliency Initiative, covering four areas of focus:- Strengthen reliability based on learnings from the incident we saw in July.
- Enabling more apps and users to run without admin privileges.
- Stronger controls for what apps and drivers are allowed to run.
- Improved identity protection to prevent phishing attacks.
Windows 11 Secure by Default: More Secure than Windows 10
Moving to Windows 11 provides a more protected environment with advanced security features. We are intently focused on raising the bar to ensure robust defense against sophisticated attacks. All new Windows 11 PCs require a hardware-backed security baseline, such as TPM 2.0 and virtualization-based security by default. This baseline is the starting point, and the foundation needed to help secure everything else on Windows. Copilot+ PCs feature Windows Hello Enhanced Sign-in Security, and the built-in Microsoft Pluton security processor, ensuring they meet the high standards of secured-core PCs by default. Built into new Windows 11 PCs, including Copilot+ PCs, are a growing list of existing features now enabled by default, or with additional protections added to significantly reduce the potential for attacks. These changes make Windows 11 more secure by default than Windows 10, from the chip to the cloud. Examples include Credential Guard, vulnerable driver block list, Local Security Authority (LSA) protection now enabled by default for new consumer devices, and BitLocker enabled by default on most modern systems. In addition, insecure code and crypto algorithms have been removed, and kernel attack surfaces, like Tool Tips, have been moved to user mode. Our security teams are working hard for you, so you don’t need to spend your time manually enabling security on new or upgraded PCs. Our focused security work, driven by observing attacker patterns and behaviors, has resulted in a reported 62% drop in security incidents and a threefold reduction in firmware attacks and 2.9 times fewer instances of identity theft reported.1New Windows 11 Security
Security is a pursuit, and not a destination. Today, I am announcing new features to help commercial customers with three longstanding challenges with Windows security — overprivileged users and applications; unverified apps and drivers; and insecure credentials and authentications. These capabilities have been top requests from customers around the world, including our internal Microsoft security team who we are working with to ensure real-world testing in preparation for scaling to our largest customers.Reducing Administrator Privileges
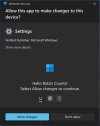
Running users and apps as administrator violated the principle of least privilege and leads to many security incidents. As noted in the 2024 Microsoft Digital Defense Report, token theft incidents, which abuse user’s privileges, have grown to an estimated 39,000 per day1. With that in mind, organizations today have a complex binary challenge when setting up policy for employees. The choice is between having users with standard user permissions or users with administrator permissions. By choosing to run with administrator permissions, you can do every modification you need — like adjusting the time-zone, making registry changes, installing applications and many other tasks without friction. However, the bad news is that if malware infects your account, it then also has direct access to critical system resources, and can silently make changes that cause disruption, result in data loss, or worse. By contrast, standard user permission offers better security. User access to critical system resources is blocked by default, and it helps block malware or apps from silently changing machine configurations. However, standard user permission is frustrating for users as they cannot do some common tasks like changing the time settings or installing productivity applications, because in many cases a standard user will not have the administrator credential. Standard user permission also creates an additional overhead for IT to help users with acceptable tasks, unless they have tools such as Microsoft Intune Endpoint Privilege Management.- Administrator protection, currently in preview, is a new solution where users have the security of standard user permissions by default, but can still easily make system changes, including app installation, on their PCs when needed. With administrator protection, if a system change requires administrator rights, like some app installations, the user is prompted to securely authorize the change using Windows Hello. Windows creates a temporary isolated admin token to get the job done. This temporary token is immediately destroyed once the task is complete, ensuring that admin privileges do not persist. Administrator protection helps ensure that users, and not malware, remain in control of system resources. It will also be disruptive to attackers as they no longer have automatic, direct access to the kernel or other critical system security without specific Windows Hello authorization.
 User prompts for authorizing admin operations[/caption]
User prompts for authorizing admin operations[/caption]Protecting Credentials
Credential and identity theft is a prime focus of cyberattacks. In fact, Microsoft Entra data shows that of more than 600 million identity attacks per day, more than 99% are password-based2. And our findings reveal that Multifactor Authentication (MFA) offers outstanding protection, with over 99.99% of MFA-enabled accounts remaining secure during the investigation period3. We continue to add additional protection for credentials and authentications.- Windows Hello is the built-in MFA solution on Windows. It has been further hardened and extended to support passkeys. You no longer need to choose between a simple sign-in and a safe sign-in. Windows Hello is also being used to protect Recall and Personal Data Encryption.
Trusted Apps and Drivers
Many attacks occur due to users downloading unsafe or unsigned apps and drivers. We continue to add protections to help you defend yourself and your organization from malicious apps and drivers.- Smart App Control and App Control for Business policies provide peace of mind that only verified apps can run on your device. This eliminates attacks like malicious attachments or social engineered malware. With the power of AI, we’ve made it much simpler to deploy. IT admins can simply select the ‘signed and reputable policy’ template in the app control wizard. This enables millions of verified apps to run regardless of the deployment location. Line of business apps unknown to Microsoft can be easily added by the IT admin through policy changes or via Microsoft Intune managed app deployments.
- Windows Protected Print works seamlessly with Mopria-certified devices and does not require third-party drivers. It is designed to mitigate many of the past security issues with print drivers, and offers a more streamlined experience.
Data Protection
Your commercial data is one of the most important assets for your business, and we are providing more encryption options, including Personal Data Encryption.- Personal Data Encryption for known folders is a new Windows 11 Enterprise capability using Windows Hello authentication to help protect files stored in the Desktop, Documents and Pictures folders. Protection is indicated by the lock icon on the file. With Personal Data Encryption enabled, a device administrator won't be able to view file content, as the files remain encrypted until you authenticate with Windows Hello. An IT admin, using Microsoft Intune (or another management tool) can select all or a subset of these folders to apply Personal Data Encryption. It integrates with OneDrive and SharePoint on Microsoft 365 to allow for easy collaboration. Personal Data Encryption can be used independently of BitLocker, or other solutions, and when combined with BitLocker, it offers double encryption protection. Enterprise developers can also leverage the Personal Data Encryption API to extend protection of their application data.
OS Management and Configuration
In addition to evolving security features, we continue to evolve tools to enable IT to manage and configure Windows at scale.- Hotpatch in Windows is being introduced for Windows 11 Enterprise 24H2 and Windows 365. This revolutionary feature allows businesses to apply critical security updates without requiring a system restart, shortening your time to adopt critical security updates by up to 60% from the moment a security update is offered. With hotpatching through your Windows Autopatch settings in Microsoft Intune, you can reduce the number of system restarts for Windows updates from 12 times a year to just four, minimizing security risk while keeping systems secure and productivity uninterrupted. This means consistent protection, and a streamlined, seamless experience for your users. Hotpatch in Windows is currently in preview.
- Zero Trust DNS. Network destinations are often defined by domain names, making enforcement challenging. Zero Trust DNS restricts Windows devices to approved domains, blocking outbound IPv4 and IPv6 traffic unless resolved by a Protected DNS server or allowed by IT admin. Learn more about the Zero Trust DNS preview.
- Config Refresh, available now, is a frequently requested feature as configuration drift can occur when a user or app makes changes to a PCs system registry. Config Refresh helps enforce MDM-defined security policies by automatically returning PC settings to the preferred configuration. Config Refresh works locally on the PC without needing to connect to the MDM, so devices can self-manage settings drift even when offline.
Security and Innovation for a Reliable Digital Future
Nearly 40 years after its launch, Windows continues to evolve to meet the challenges of the ever-changing digital landscape and delivering on expectations for reliability and security. Security is a team effort; by collaborating with OEM partners, app developers and others we deliver Windows from chip to cloud, secure by design and default. The updated Windows Security book is available to help you understand how to stay secure with Windows. Learn more about Windows 11 and Copilot+ PCs. To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.Continue reading...